How to Delegate Control in Active Directory Users and Computers
How to Delegate Control in Active Directory Users and Computers
In this article we’ll learn the steps to delegate control in Active Directory Users and Computers. In Organizations, delegate control is given to the help-desk representative to perform the tasks of reset password, add computer or server in domain, create new user, etc. In a domain, domain administrator is a user who can perform all operations and tasks related to domain and Active Directory. Domain Administrator is a member of Domain Admins group and also a user who is not available 24 x 7 x 365. So, the question is when the domain administrator is not available then who will manage the Active Directory.
First option is that, we will add any other user into the Domain Admins group. This would assign Domain Admin permissions to the newly added user, these rights are sufficient to perform any domain level change in the environment. But do you really want to give keys of kingdom to anyone? In my opinion, this is not the right way of delegating control.
There is an another option of Delegate Control using Active Directory Users and Computers, through which we can deploy customized access and permissions for the domain users. Through this, users can perform the tasks that Administrator is designated to perform.
Steps to Delegate Control to Domain Users
We’ll create group of users, to whom we’ll delegate rights to manage user accounts. It is recommended to delegate access to groups instead of delegating permissions to an individual users.
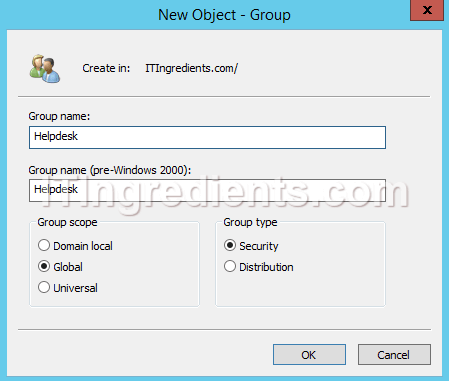
1. Open Active Directory Users and Computers, right click on an Organizational Unit (Sales) on which we have to delegate control and then click on “New” and click on Group to create a new group.
2. On New Object-Group console, enter the group name, select Global and Security options from the given options in group scope and group type respectively. Click on ok. In this example, we will create a group naming Helpdesk.
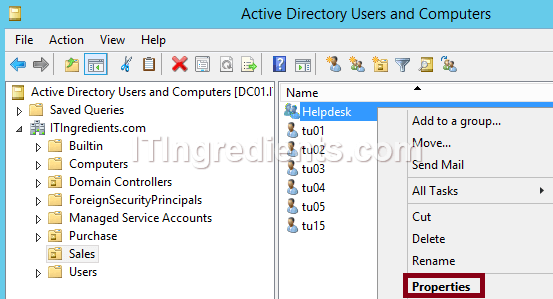
3. Right click on the group (Helpdesk) and click on Properties to open the properties console to modify various group settings.
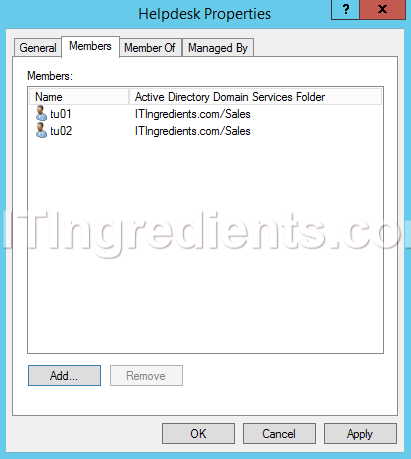
4. On Group Properties console, under members tab click on Add to add users into this group. Verify all the added users. Now, these users are the group members of Helpdesk group.
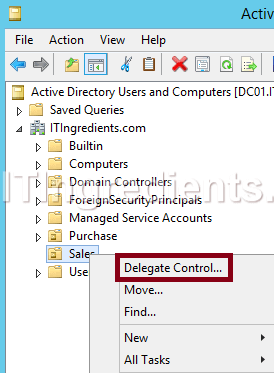
5. Right click on the Organizational Unit (Sales) and click on Delegate Control to delegate the customized permissions to the user or a group of users. This wizard will only delegate access for Sales OU and not for other OUs.
6. On the “Delegation of Control Wizard” we can see the relevance of delegate control. We can grant users permission to manage users, computers, groups, OU and other objects of AD Users and Computers. Click on Next to continue.
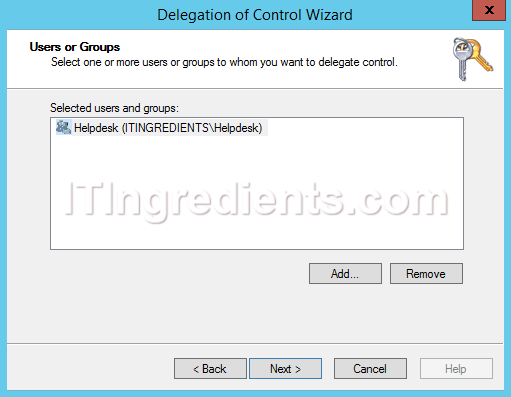
7. In users and groups console, click on Add to add the group. Here, we have added Helpdesk group so that we can assign permissions to the group members. Click on next to continue.
8. In Tasks to Delegate console, select “delegate the following common tasks” and select permissions from the given tasks. Or select the “Create a custom task to delegate” to give custom permissions to the users other than the above permissions. Click on Next to continue. For this example, we’ll delegate control for “create, delete and manage user accounts” and “Reset user passwords and force password change at next logon”.
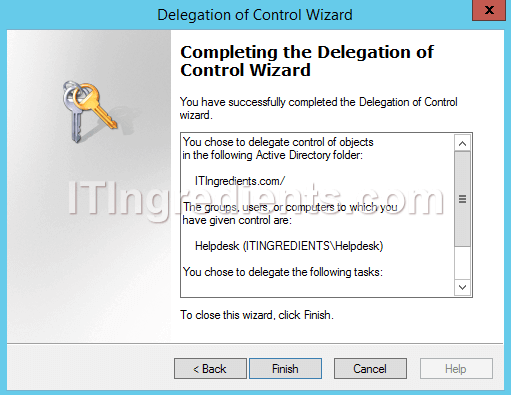
9. On the “Completing the Delegation of Control Wizard” verify the selected options on previous consoles and click on Finish to close the console.
A user (TU1) is a member of Helpdesk Group and have delegated permissions. But these rights would not enable domain user to login to Domain Controller. This user cannot access Active Directory Users and Computers either by login to Domain Controller or using RDP from any client machine e.g. Windows 8.1 operating system because he is not a member of Domain Admins group.
To enable user to access Active Directory users and computers from client machine, we need to install the Active Directory Domain Services role on Windows 8.1 client, to install the role, install the windows update package (Windows8.1-KB2693643-x64). You can download this update package from the given link (http://www.microsoft.com/en-us/download/details.aspx?id=39296).
1. After installing this package, we can see the icon of Active Directory Users and Computers in the start menu under Administrative Tools on Windows 8.1 Operating System. Click on the icon of AD Users and Computers to open the console.
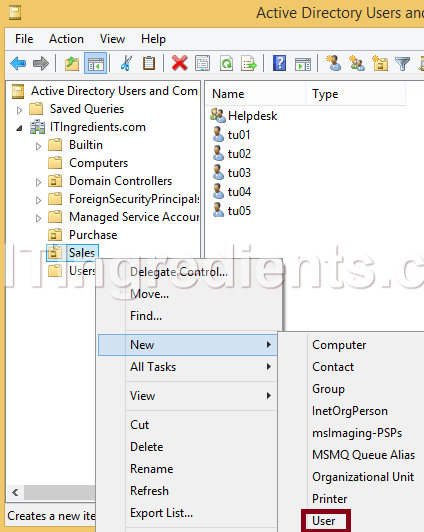
2. Through this console, this user (TU01) can only perform the operations that we have delegated to “Helpdesk Group”. Learn how to create user. We will try to create a new user in the Organizational Unit (Sales) to the check that given permissions are delegated successfully or not. Right click on the OU (Sales) and then click on New and then User to create a new user.
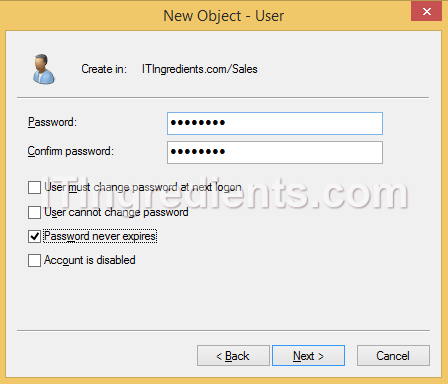
3. On New Object – User console, enter the details like First name, Last Name, User logon name of the new user which you want to create. Click on Next to continue.
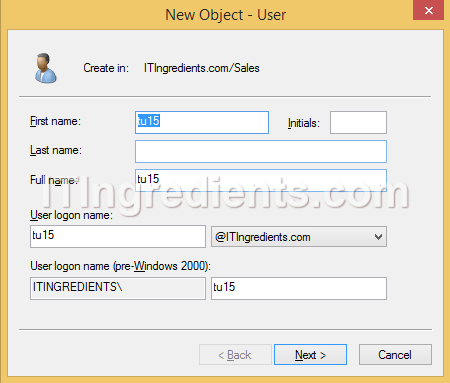
4. Enter the password in the Password and Confirm Password field of the user which we are creating and select the option according to your requirement from the given options. Click on Next to continue. On the next console verify all the settings and then click on Finish.
5. On Active Directory Users and Computers, in Sales OU we can verify that user tu15 is successfully created. It clearly shows that rights are successfully delegated to the user tu01 through the security group helpdesk.
This user (TU01) can perform other delegated rights e.g. resetting user account password, deleting user account and other similar operations.
Conclusion:
Delegate access would enable set of users to perform the tasks that are normally performed by Domain Admins. It would only restrict the user to the OU on which rights are delegated.






Hi Mr. RaakeshKapoor,
Your post is very useful for me. I am new to active directory. Now i am very much clear about delegation. And one doubt strike in my mind when i read this post. whether the delegated user can perform changes in that particular user group or particular organisation unit only or can make changes to all the users account through out the domain.
Delegated user can perform all the delegated task only within the OU for this delegation is defined. This means, delegated user can manage all the objects within that OU. Hope it answers your question.
Hello.
Thank you for the user guide.
I followed your instructions and delegated control over an OU to an account. The strange thing is that when I try to create a user in that OU with that user account nothing happens… no window prompts with the new account information, no error message, nothing…
I’m doing the tests on a windows 10 virtual machine.
If I do the same test on my laptop, it works……..
Both VM and my laptop are joined to the domain.
Any ideas?
Thanks for your help!
Cheers!
Did you try log off the user and then login back to whom you have delegated the permission?